
Call the experts in Long Island Computer Virus Removal, Spyware Cleanu. When your computer has a Virus, Malware, Spyware, Hijack or some other type of trojan virus, you will inevitably find yourself in a frustrating situation. You might be unable to use your computer at all, or your computer may just slow down considerably. Some viruses even steal your information and send out emails and other messages to the contacts in your personal account. If your computer has spyware or a virus, you might not even be able to install a new Anti-Virus program. The virus or spyware may freeze your whole computer up. We at techsonduty are a staff of certified experts who are here to help you remove viruses, malware, spyware, and other security threats from your computer, and make sure you don’t have the problem come up again. Our virus removal experts will do the following:
- Scan your computer and determine if it has been infected by viruses or spyware
- Locate viruses and Trojans present on your computer
- Remove any and all viruses, spyware/malware
- Manually perform repairs to your computer registry (this will allow us to install a reliable Anti-Virus program for you)
- Install Anti-Virus program
- Perform updates on your Operating System and major Software apps
- Configure your Anti-Virus and Spyware removal tool
- Run your first Anti-Virus Spyware removal program scan
- Clean the computer
Computer Virus Removal, Spyware Cleanups across Long Island
Sometimes, computer spyware is included along with genuine software, and may come from an official software vendor. In an attempt to increase the understanding of computer spyware, a more formal classification of its included software types is provided by the term privacy-invasive software. In response to the emergence of spyware, a small industry has sprung up dealing in anti-spyware software. Running anti-spyware software has become a widely recognized element of computer securitypractices for computers, especially those running Microsoft Windows. A number of jurisdictions have passed anti-spyware laws, which usually target any software that is surreptitiously installed to control a user’s computer.
Cyber criminals often updated the design of this lock screen, however you should always keep in mind that the Federal Bureau of Investigation will never lock down your computer or monitor your online activities.
The message displayed by the threat can be localized depending on the user’s location, with text written in the appropriate language.
The FBI virus is a scam, and you should ignore any alerts that this malicious software might generate.
Under no circumstance should you send any MoneyPak code to these cyber criminals, and if you have, you can should request a refund, stating that you are the victim of a computer virus and scam.
FBI lock screen – Virus Removal Guide
This page is a comprehensive guide, which will remove the FBI infection from your your computer. Please perform all the steps in the correct order. If you have any questions or doubt at any pointSTOP and ask for our assistance.
The FBI will start automatically when you login to your computer and display its screen locker so that you are unable to access your computer, therefore we will need to remove this infection by using one of the below methods:
OPTION 1: Remove FBI lock screen virus with System Restore
OPTION 2: Remove FBI virus with with Malewarebytes
OPTION 3: Remove FBI virus with Kaspersky Rescue Disk
OPTION 1: Remove FBI lock screen virus with System Restore
System Restore helps you restore your computer’s system files to an earlier point in time. It’s a way to undo system changes to your computer without affecting your personal files, such as e‑mail, documents, or photos.
Because the FBI virus will not allow you to start the computer in Windows regular mode, we will need to start System Restore from the Safe Mode with Command Prompt mode.
STEP 1: Restore Windows to a previous state using System Restore
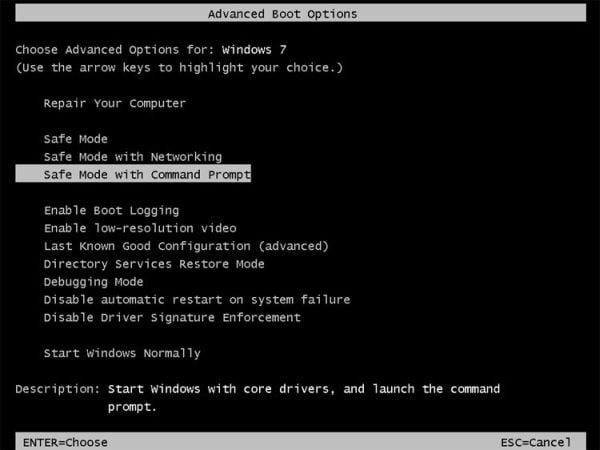
 Reboot your computer into Safe Mode with Command Prompt. To do this, turn your computer off and then back on and immediately when you see anything on the screen, start tapping theF8 key on your keyboard.
Reboot your computer into Safe Mode with Command Prompt. To do this, turn your computer off and then back on and immediately when you see anything on the screen, start tapping theF8 key on your keyboard.
If you are using Windows 8, the trick is to hold the Shift button and gently tap the F8 key repeatedly, this will sometimes boot you into the new advanced “recovery mode”, where you can choose to see advanced repair options. On the next screen, you will need to click on theTroubleshoot option, then select Advanced Options and select Windows Startup Settings. Click on the Restart button, and you should now be able to see the Advanced Boot Options screen.- Using the arrow keys on your keyboard, select Safe Mode with Command Prompt and press Enter on your keyboard.
- At the command prompt, type rstrui.exe, and then press ENTER.
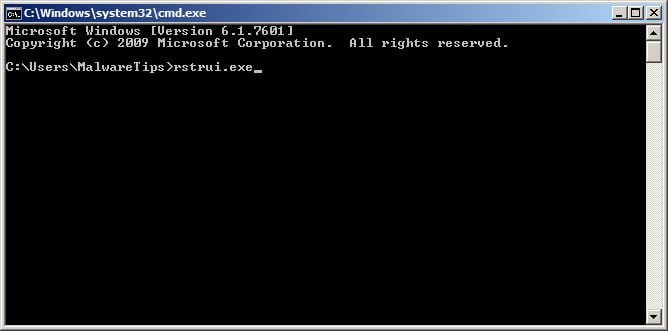
Alternatively, if you are using Windows Vista, 7 and 8, you can type:C:\windows\system32\rstrui.exe , and press Enter. And if you are a Windows XP user, type C:\windows\system32\restore\rstrui.exe, then press Enter. - System Restore should start, and you will display also a list of restore points. Try using a restore point created just before the date and time the FBI lock screen virus has infected your computer.
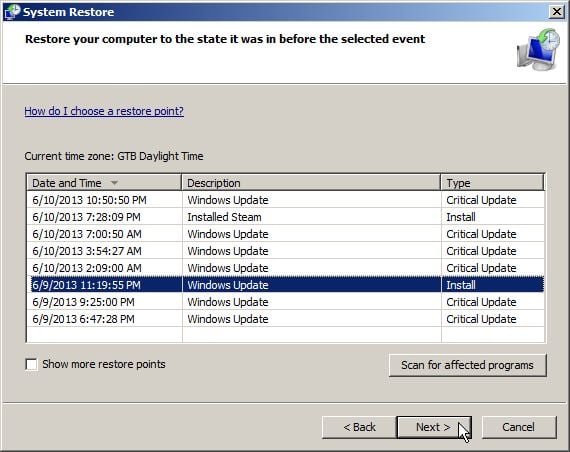
- When System Restore has completed its task, start your computer in Windows regular mode, and perform a scan with Malwarebytes Anti-Malware and HitmanPro, as seen in the next step.
STEP 2: Remove FBI malicious files with Malwarebytes Anti-Malware Free
Even after using System Restore,
- You can download Malwarebytes Anti-Malware Free from the below link, then double-click on the icon named mbam-setup.exe to install this program.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK(This link will open a download page in a new window from where you can download Malwarebytes Anti-Malware Free) - When the installation begins, keep following the prompts in order to continue with the setup process, then at the last screen click on the Finish button.
Long Island Computer Virus Removal, Spyware Cleanup
Sometimes the truth hurts, but here it is anyway: You will struggle with spyware at work, home, and on family and friends’ computers for the next several years. Spam will be choked down to a manageable stream this year, but spyware will fill the gap, costing you precious hours cleaning the infected (and re-infected) computers of your friends and family.The bottom line is they’re all good; they all help. But they’re all incomplete. Running anti-spyware utilities is just part of the solution. There are a slew of other things you can do, and have your users do, to curb the problem. Follow our handy 10-step guide to get started.
If you define spyware as any tiny cookie left behind by an innocent Web site, your frustration will never end. Scumware of all kinds will cause you grief, but the four major types are:
Spyware: an application surreptitiously gathering information about your computing habits that may send the data to some unknown site – aka “key loggers” or “keystroke capture parasites.” (Not to be confused with “malware,” which includes viruses, worms and Trojan horse programs.)
Adware: an application that pops up advertisement windows and banners randomly or based on current browser content – aka “pop-ups.”
Hijackers: applications that change your browser home page, default search engine and even redirect you from sites you try to reach – aka “jackers” or “switchers.”
Cookies: small files that track data such as Web site preferences and passwords for repeat visits. Spyware gathers and spreads this information without user knowledge – aka “tracking cookies.”
Adware is the most annoying, but hijackers and spyware do the most damage. Scumware purveyors claim we all “agree” to their garbage, but of course we don’t. Yet, a lot of this stuff is harmless; teach your friends to tolerate a few cookies and save the 911 calls for aggressive pop-ups, browser home page redirects and suddenly sluggish systems.
Get off Internet Explorer
We can’t charge Microsoft with a crime for creating spyware. But the design of Windows, and particularly Internet Explorer, certainly makes it an accessory. Encourage friends and family to switch to alternatives Firefox or Opera, which both block pop-ups by default. Firefox is free and available here; Opera costs a few dollars.
Need proof Internet Explorer is the problem? On my primary test PC running Windows XP Home, I use Internet Explorer and Outlook Express. There were 739 spyware threats found. On my personal PC, running Firefox and Mozilla’s Thunderbird e-mail application, there were 11 spyware instances. Each of those 11 was an Internet Explorer exploit or cookie that snuck in the few times I had to use Internet Explorer for certain Web sites.
But Microsoft is now making noise about anti-spyware tools (see “Giant Microsoft improvement?” next page), and XP Service Pack 2 has reduced the ability for most spyware to cripple a system completely.
Unfortunately, some sites demand Internet Explorer, and users who are heavily intertwined with Microsoft’s Outlook e-mail client must use it. But there are ways to slow spyware using Internet Explorer. First, disable Microsoft ActiveX support. In Internet Explorer, click on Tools > Internet Options > Security > Custom Level, then click the check boxes that force ActiveX controls to ask permission before running.
Next, install the Google Toolbar, which also blocks pop-ups. It works on Internet Explorer 5.5 and higher, so you might have to upgrade the browser. Also, run pop-up blockers designed to work inside Internet Explorer, such as StopZilla, 123Ghosts Popup Killer, Ad Killer, Ad Muncher and Anti Popup Pro .
Deter downloads.
Walk this line carefully: Don’t let friends and family – especially the tech neophytes like your grandmother – download anything. Then download and install the Google Toolbar for them. Explain why it’s different from the weather station and smiley faces for their e-mails.
People want to download “free” programs from the Web, but teach them the difference between a site they visit for utilities (such as PCWorld.com or Tucows.com ) vs. sites that appear in pop-up ads and spam.
Resolve not to get frustrated; accept that education will only work halfway. Spyware purveyors do a wonderful job convincing innocents to download spyware daily. Explain how what looks like a Google ad on the side of a browser page, or the link their good buddy sent them, is really a social engineering masterpiece of spyware diffusion. Sensitize your users to the most obvious danger signs, such as banner ads popping up offering a free spyware check (a cruel abuse of trust).
Teach back-up and restore basics.
Because many users won’t heed your warnings, teach them how to recover from download disasters. People have too much on their computers today to resist back-up options. An external hard disk, tape system or CD writer full of back-up data can ease the sting of a spyware-ridden system and put things right with a restore to an earlier, spyware-free back-up point.
Teach users how to create restore points in XP and to set one before every download from a Web site that’s not a brand-name portal. Disk space shouldn’t be a problem on newer PCs, but even if they fill up their hard disks, eliminating some restore points is much easier than cleaning a spyware infection.
Create a spyware removal CD.
Remember your Boy Scout days and be prepared for the next call for help. Make your own spyware tool kit by burning a half-dozen spyware utilities to CD. When you go to clean a spyware machine, finding and waiting for utilities to download wastes time that’s better spent with your own family. CD-ROM disks are inexpensive, so make extra copies and give them to your users. On mine, I have three free utilities, with three trial versions of commercial utilities. The programs range from 2M to 10M bytes, so you’ll have plenty of room on a standard CD.
Located in Valley Stream – Techsonduty provides service to surrounding towns like Lynbrook, Malverne, Elmont, Woodmere, New Hyde Park, Franklin Square, Mineola, Hewlett, Freeport, Rosedale, Manhasset, Lake Success, Floral Park, Queens Village, Rockville Centre, and East Rockaway.
Call Today for support – 516-360-0757

